What are the actions taken by the Crypted virus?
Crypted Virus, also known as Crypted ransomware which is a dangerous computer infection. This virus can be installed on a computer system without the user's knowledge, and run the exe file when the user restarts the next computer. This exe file scans the entire computer system and looks for files with certain file extensions. Reportedly, this virus looks for audio files, videos, music files, images, documents and other files needed, then it will encrypt them using sophisticated encryption algorithms. In addition, it will add the .crypted file extension behind the file name.After that, the virus left ransom notes on several computer folders. This ransom states the victim's encrypted file record and guidance on buying the decryption key that can be used to restore your data. Just like other ransomware, the Crypted virus command is to use The Onion Router, also known as TOR software and make payments at Bitcoins.
However, if you are a victim of Crypted ransomware, we do not recommend that you pay a ransom. First of all, you can never know whether cybercriminals will really provide the decryption key, or they just want to steal your money; Second, think back if you want to support cybercriminals. The more ransom they collect, the more motivated they are in hijacking you.
It is almost impossible to break the encryption algorithm that uses a ransomware virus; Therefore, it is not possible to decrypt files without decryption keys. However, you can still try the following tools to decrypt your files - Photorec, R-Studio or Kaspersky virus-fighting utilities.
If you backed up your files some time ago on your external drive, you can import them to your computer, but before you do, delete Crypted malware from your system completely. We recommend scanning your computer system with the leading anti-malware tool - Reimage, and seeing if this virus has been installed for every other computer threat on the PC. After the scan, you can delete all detected threats with one click.
How does Crypted spread?
Crypted usually spreads via contagious email: cybercriminals send fake e-mails that contain attachments. It's important to check if you know who the sender of the email is before you open it or attach it. Usually, fraudsters pretend to provide relevant documents, for example, invoices, price charts, bills, resumes and so on. Watch Out; and leave the Spam / Trash folder, this is where this email is usually.You should pay attention when browsing the internet, cybercriminals tend to spread dangerous files and programs by hiding dangerous links on several sites. Try to avoid suspicious websites, and refrain from clicking on annoying pop-up ads or banners. Also, avoid downloading files from insecure file-sharing networks. You might install a Trojan horse on your computer without realizing it; reportedly, a trojan named JS. Nemucod spread this ransomware, as well as other well-known viruses, such as Locky, Teslacrypt, KeRanger, and others.
How to delete Crypted ransomware?
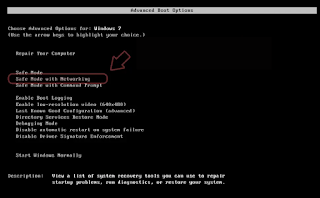
Crypted removal is a difficult process; ransomware is a complex and well-built virus, which hides its components very deeply on a computer system. In addition, the components of the virus use names that sound safe, which makes it more difficult to identify them. For this reason, we recommend that you install a professional malware removal tool and stop all programs and processes related to it. We recommend using Reimage or other top malware removal software. When you want to delete the Crypted ransomware manually, follow these steps:Step 1: Reboot your computer into Safe Mode with Networking
Windows 7 / Vista / XPClick Start → Shutdown → Restart → OK.
When your computer is on, start pressing F8 several times until you see the Advanced Boot Options window.
Select Safe Mode with Networking from the list
Windows 10 / Windows 8
Press the Power button on the Windows login window. Now press and hold Shift which is on your keyboard and click Restart...
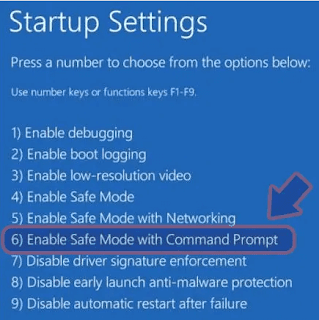
Now choose Troubleshoot → Advanced options → Startup Settings and finally press Restart.
When your computer is active, press Enable Safe Mode with Networking in the Startup Settings window.
Step 2: Remove Crypted
Login to the infected account and open your browser. Download Reimage or other legitimate anti-spyware programs. Update the program before scanning the system and removing the malicious files from the ransomware and completing Reimage removal.If the ransomware is blocking Safe Mode with Networking, try several methods.
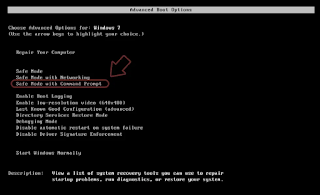
Step 1: Reboot your computer into Safe Mode with Command Prompt
Windows 7 / Vista / XPClick Start → Shutdown → Restart → OK.
When your computer is on, start pressing F8 several times until you see the Advanced Boot Options window.
Select Command Prompt from the list
Windows 10 / Windows 8
Press the Power button on the Windows login window. Now press and hold Shift which is on your keyboard and click Restart...
Now choose Troubleshoot → Advanced options → Startup Settings and finally press Restart.
When your computer is active, press Enable Safe Mode with Command Prompt in the Startup Settings window.
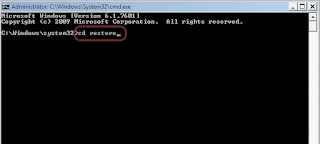
Step 2: Restore your system files and settings
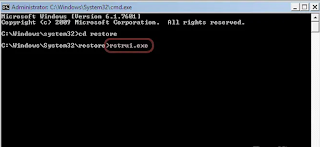
When the Command Prompt window appears, enter cd restore and click Enter.Now type rstrui.exe and press Enter again...
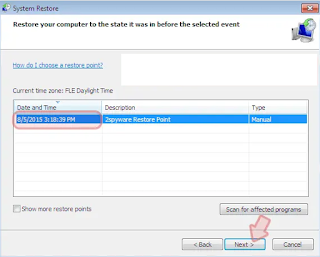
When a new window appears, click Next and select your restore point that is prioritized on piracy from Crypted. After that, click Next.
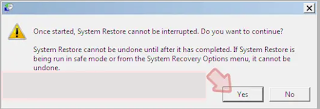
Now click Yes to begin system restore.
After you restore your system to a previous date, download and scan your computer with Reimage and ensure that the Crypted removal is successful.
Finally, you should always think about protecting crypto-ransomware. To protect your computer from Crypted and other ransomware, use reputable anti-spyware, such as Reimage, SpyHunter 5 or Malwarebytes.